Just as the DevOps philosophy ensures development and operations teams break out of silos to collaborate on software development, so does DevSecOps remind us that security teams should be included in these collaborative spaces as well.
With security compliance an integral part of the software development lifecycle, it stands to reason that shift-left testing should extend to security. Including security teams early in the development process ensures DevOps teams maintain the integrity of software compliance requirements from project initiation through delivery. The software lifecycle is most efficient when the culture of shared responsibility drives teams at all stages to consider security concerns.
Sauce Labs’ Marcus Merrell predicted 2023 would see more widespread security testing happening in parallel with application development, rather than at the end. And the trend is proving promising for this forecast – the DevSecOps market generated $2.55 billion in 2020 and is expected to notch a compound annual growth rate (CAGR) of 32.2% through 2028.
To properly protect the integrity of software builds, a DevSecOps approach brings DevOps teams to the security and compliance table, ensuring they understand the requirements and share responsibility for enforcing security policies throughout development and deployment.
What is DevSecOps?
The role of security has historically been tasked to a specific team in the final stages of software development. Thanks to the success of the DevOps model, it’s become more apparent that security functions benefit from the collaborative practice of that framework. Dubbed DevSecOps (or occasionally Secure DevOps), the resulting model dictates that application and infrastructure security are considered a collective responsibility that is addressed at all parts of the development cycle. Security issues can be addressed as they emerge – when they’re faster, easier, and less expensive to fix – instead of after a product goes into production.
With DevSecOps, automating some of the security processes is necessary to keep the workflow moving quickly. Utilizing new tools that are increasingly being used for this purpose, and combined with the culture change of DevOps, security can be thought of as an integral part of the development lifecycle and not a peripheral function. Bringing security teams into the DevOps circle allows them to plan automation, and can also lead to new security training for developers who might not have previously had the opportunity to focus on security during development.
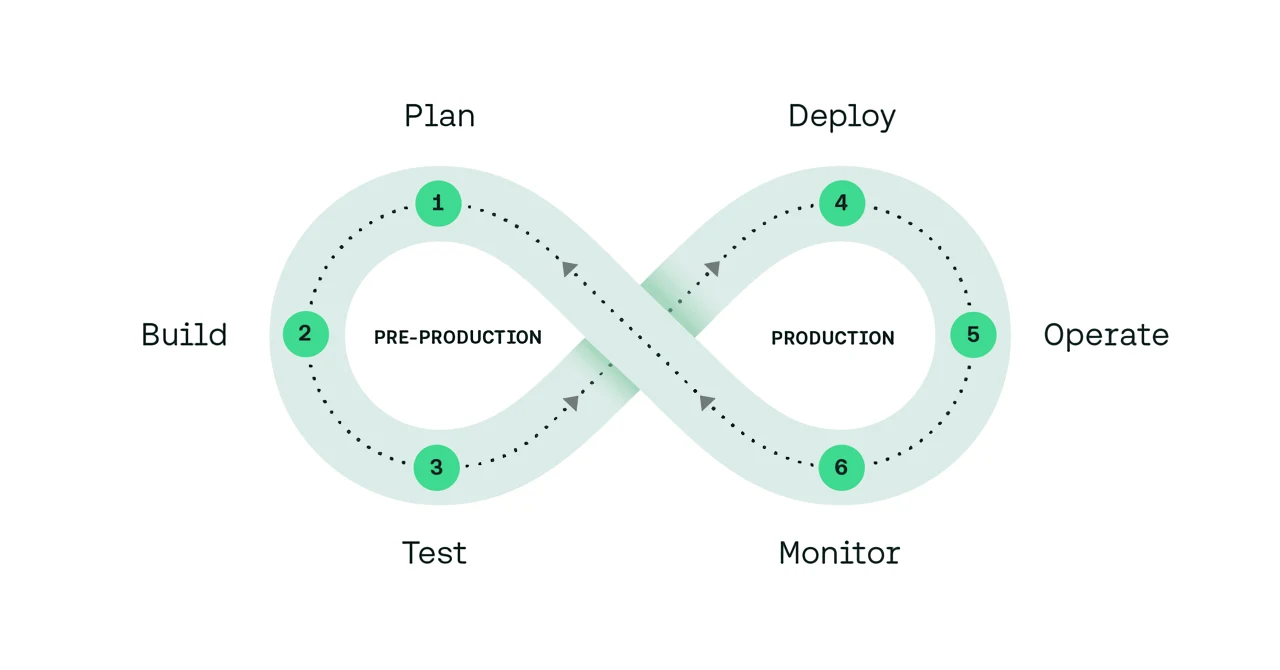
What is the DevSecOps lifecycle?
With an agile approach to development, teams using DevSecOps frameworks apply security protocols and tests at multiple points in the lifecycle, aiming to solve security issues early so that they are not only easier to fix, but also help avoid launch delays that stem from unexpected complications. The power of automation at each step should help ensure the entire process is supporting security rather than being held back because of it.
Plan – the least automated phase of DevSecOps, planning involves performing a security analysis and creating a plan that outlines how, where, and when security testing will be done. A good DevSecOps strategy starts with determining risk tolerance and risk/benefit analyses.
Build – Once developers commit code to a source repository, automated security practices include software component analysis, static application software testing, and unit testing. It’s important to scan any third-party code dependencies for vulnerabilities.
Test – After the build artifact is successfully deployed to a staging environment, a comprehensive test phase using dynamic application security testing (DAST) detects live application flaws like user authentication, authorization, API-related endpoints, and SQL injection.
Deploy – During the deployment phase, the areas to apply security checks are those that only happen against the live production system, such as differences in configuration between the production environment and the previous staging environments. Additionally, runtime verification tools can determine whether a system performs as expected, and teams may choose to test turbulent conditions such as server crashes, hard drive failures, or severed network connections.
Observe – Organizations need to monitor and observe the live application for attacks or leaks, using automated security checks and security monitoring loops. To boost these tasks, special teams may perform penetration testing to identify exploits or vulnerabilities by deliberately compromising a system, or companies may pay bug bounties to individuals who report vulnerabilities.
What are DevSecOps best practices?
The priority in DevSecOps is to integrate security measures with minimal disruption to operations, contributing to maintaining short and frequent development cycles. This comes from automation, looking at what in the whole development and operations environment can be most efficiently automated – things like source control repositories, management of the application programming interface, container registries, the continuous integration (CI) and continuous development (CD) pipeline, operational management, and more.
A few specific practices of an effective DevSecOps framework include:
Security education – Standardize the organization’s security protocols by educating all teams on the processes they will be collectively using.
Integrate the right tools – Recent tech like containers and microservices are a big part of DevOps and the security operations must adapt to include them.
Scan and secure components and tools – Whether they’re open-source or third-party, make sure you are verifying the security of any tool that’s part of your process.
Centralize user identity and access control capabilities – Apply the principle of least privilege (PoLP) to ensure any user, program, or process (such as API keys or access tokens) has minimum access to perform its function.
Organizational culture – Promote change within the organization with supportive leadership and a policy of communication; make developers and engineers process owners who take care of and are invested in their work. Allow teams to develop their own processes that fit their workflow environment.
Deeper process insight – Create a more secure environment by implementing traceability, auditability, and visibility into your DevSecOps processes.
What are the Benefits of DevSecOps?
The largest benefits of using a DevSecOps philosophy are faster delivery and a more secure product. More specifically, improvements in collaboration, efficiency, and adaptivity work together to create an overall better product, happier teams, and flexible organizational frameworks.
Cross-team ownership – Just as in broader DevOps, DevSecOps brings together teams to use a collaborative approach, removing silos that stifle innovation and foster division amongst units. Getting teams on the same page early increases team buy-in.
Advanced, proactive application security – Continuous security testing means problems are fixed before additional dependencies are introduced, making fixes less expensive and reducing the likelihood that compliance requirements will need to include the retrofitting of projects.
Streamlined application delivery – Avoiding security-related delays that involve fixing code means delivery is more rapid and cost-effective. Integrated security cuts out duplicate reviews and unnecessary rebuilds.
Quick recovery to security incidents – DevSecOps helps improve an organization’s response to incidents and problems when they occur. By reducing the time it takes to patch vulnerabilities, the security teams are free to focus on higher-value work.
Accelerated vulnerability patching – By integrating vulnerability scanning and patching into the development and release cycle, identifying and fixing security issues happen faster, reducing the window given to threat actors to take advantage of vulnerabilities.
Long-term processes – The automation and priority of security processes mean organizations using DevSecOps have more scalable and adaptive processes that can ensure consistency within any environmental change.
What are the Tools Used in DevSecOps?
Successful DevSecOps processes hinge on the automation of testing and monitoring. Using open source or paid tools to help automation at each step of the lifecycle helps to streamline production and create a more secure product. Primary tools include:
Static application security testing (SAST) – Automates scanning of application code to identify security risks for software, libraries, containers, or other vulnerable artifacts. Otherwise known as security composition tools (SCA) or white box testing. Some well-known tools include OWASP, SonarQube, SourceClear, and Checkmarx.
Dynamic application security testing (DAST) – Analyze application code more granularly with DAST tools, which check for cross-site scripting, SQL injections, or risks against encryption. Popular tools include BBD, JBroFuzz, Boofuzz, OWASP ZAP, Arachi, IBM AppScan, and SecApp Suite.
Interactive application security testing (IAST) – Analyze the code inside the application while a user tests specific functionality. Examples include Contrast, HCL AppScan, Invicti, and Checkmarx.
Runtime application self-protection (RASP) – Automatically identify and block inbound security threats in real-time. Examples of popular tools include Imperva RASP, Alert Logic, and Halo.
Project management – Build a backlog of projects and break them down into smaller, trackable tasks with project management tools like Scrum, Lean, Kanban, GitHub Issues, and Jira.
Communication – Ensure your teams have the right environment for collaborative, organized communications with tools like Slack and Teams.
Building Your Own Security-Aware Development Framework
The constant evolution of exploits and attackers requires a maintained vigilance in security protocols – it is imperative that modern software teams evolve to continue to meet the demands of a noisy market, addressing security considerations continually throughout the development lifecycle.